Describe Tools Used to Attack Web Servers
Flooding Mail Servers. The commonly used web servers include Apache and Internet Information Service IIS Attacks against web servers take advantage of the bugs and Misconfiguration in the.
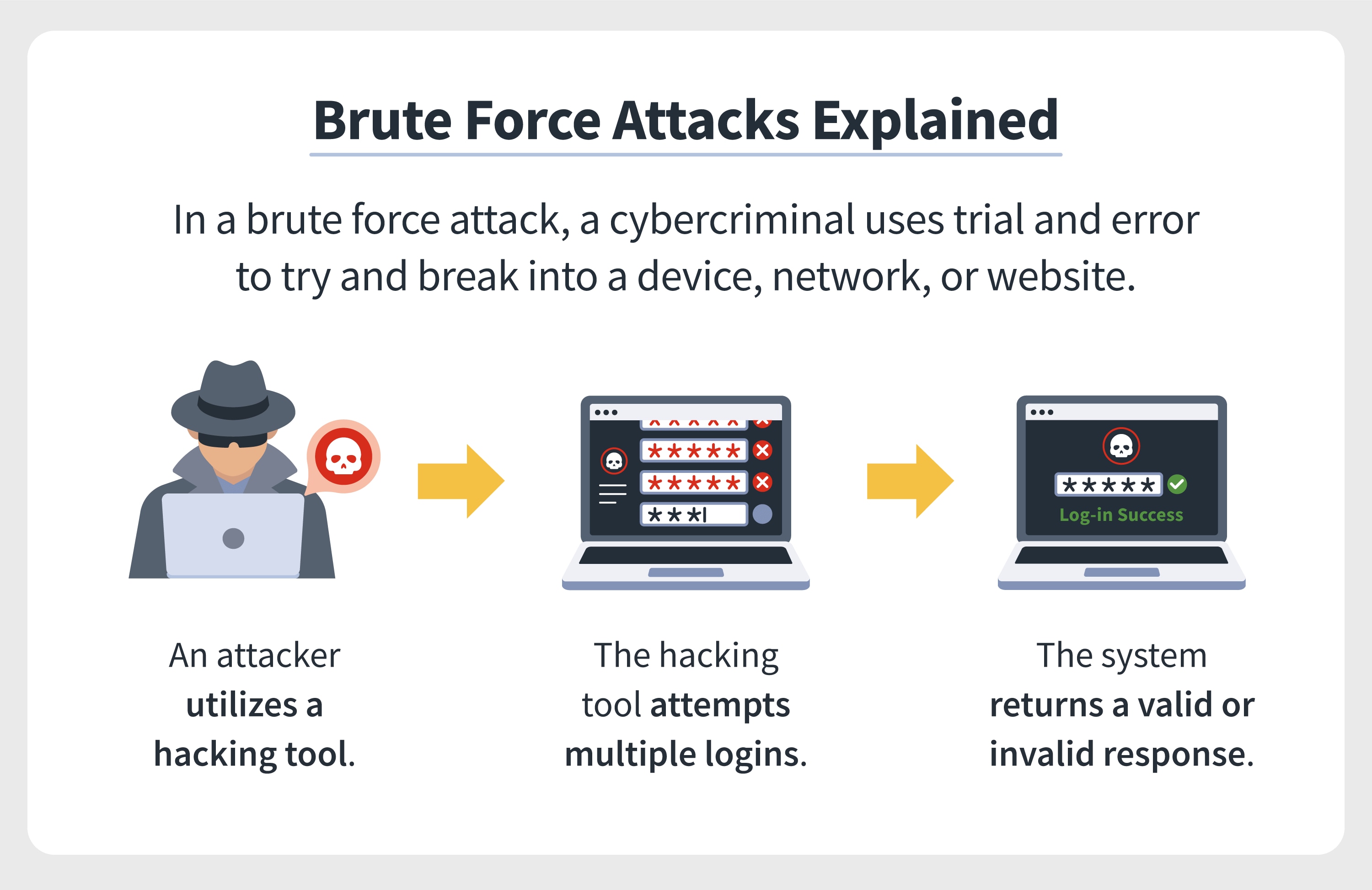
Brute Force Attack A Definition 6 Types To Know Norton
Ransomware How to prevent Network Attacks 1.
. SQL Injection SQLi At about 24 percent of web attack attempts this was the second most common attack technique we witnessed. Acunetix Nikto Vega etc. The hacker sends a command to the master which resides in any of the many hosts.
It is easy to use highly customizable and contains numerous powerful features that can help the most experienced pentesters. Provide at least three methods or tools used to attack web servers as well as provide how each of these three methods can be protected against. To simplify things most of network attackers use a powerful tools to gain access the data on a network.
Specific Server Security Tools Some of the most popular Plesk extensions are those which improve your servers security. Common Types of Network Attacks and Prevention Techniques 1. In this blog post I will describe the common.
Most XSS attacks are not particularly sophisticated and we see a lot of attacks come from so-called script kiddies who are inexperienced attackers using scripts and tools others wrote. In Distributed DoS DDoS attack a hacker installs an agent or daemon on numerous hosts. Phishing and spear phishing attacks.
Here are some of the most powerful ones which help combat server threats. Denial-of-service DoS and distributed denial-of-service DDoS attacks. The results may show various threats and vulnerabilities on the target web server.
FTP Bounce Attacks Port Scanning Attack Ping Flooding Attack Smurf Attack SYN Flooding Attack IP FragmentationOverlapping Fragment Attack IP Sequence Prediction Attack DNS Cache Poisoning SNMP Attack Send Mail Attack Some of the more popular attack methods are described below. Handpicked related content. Denial-of-Service DoS attack 7.
Most often there were Implementing SQL statements and Running OS commands. Making the use of this security vulnerability an attacker can inject scripts into the application can steal session cookies deface websites and can run malware on the victims machines. When executed the attacker inserts a piece of code that reveals hidden data and user inputs enables data modification and generally compromises the application.
This type of attack is called Cross-Site Scripting XSS attacks and may be used even though the web servers and database engine contain no vulnerability themselves. Metasploit Framework an open source tool for exploit development and penetration testing Metasploit is well known in the security community. Review the tools used to attack Web servers.
Separate Development Testing Production environment. Attackers use sniffers or protocol analyzers to capture and analyze packets. Today Ill describe the 10 most common cyber attack types.
500 words or more please. Vulnerable Objects Input Fields URLs Examples. Such attacks are used to make a point make some profit or simply for fun.
However as the popularity grows the risks grow with it and just like any protocol HTTP is vulnerable to attacks. All applications can easily be found by unwanted users. The SQL injection method is the most popular practice used by cyber criminals in this category.
Learn to strike at your targets weak points with this three-video course on attacking Web servers. It is often used in combination with other attack vectors such as social engineering attacks. The master communicates with the agents.
Computer Virus Learn more about How does a computer virus spread. We begin with the how and why of targeting Web servers including gathering useful server security information and tools such as Nessus Nikto and ScanMyServer. Making the audit easier.
Identify web application vulnerabilities and tools used to. A Vision for Strong Cybersecurity. Every attacker tries to gather as much information as possible about the target web server.
XSS is an attack which allows the attacker to execute the scripts on the victims browser. Man in the Middle MITM Attack IP Spoofing 3. This way website access network services database server and operating system logs can be monitored frequently.
Attackers try to use the most simple attacks which do not require special conditions for execution. Discuss securing web applications. There are automated tools for scanning a web server and applications running on it.
Monitor and audit the server. In other works it is an excellent tool for performing web application security assessments. This code is executed by the victims and lets the attackers bypass access controls and impersonate users.
In other words a sniffer can eavesdrop on electronic conversations. The injection attack methods target the website and the servers database directly. These vulnerabilities may later be exploited using tools or manually.
Nikto is an open source GPL web server scanner which performs comprehensive tests for multiple items against web. Path Traversal was the second most popular among the detected attacks. Summary Web server stored valuable information and are accessible to the public domain.
Flooding Service Ports. This makes them targets for attackers. A popular sniffer is Wireshark and its available as a free download.
If data is sent across a network in clear text an attacker can capture the data packets and use a sniffer to read the data. Such attacks were fixed in more than 80 percent of systems. Sentinel Anti-malware Sentinel Anti-malware is a scanner that combines the open-source principles from Linux Malware Detect and ClamAV.
Attackers use Denial-of-Service DoS attack techniques in order to create denial-of-service on web servers. Web server logins should be stored in a separate area. The attacker gathers the information then analyzes the information so as to seek out lapses within the current security mechanism of the online server.
Cross-site scripting XSS is a security exploit which allows an attacker to inject into a website malicious client-side code. DoS Attacks Involve.

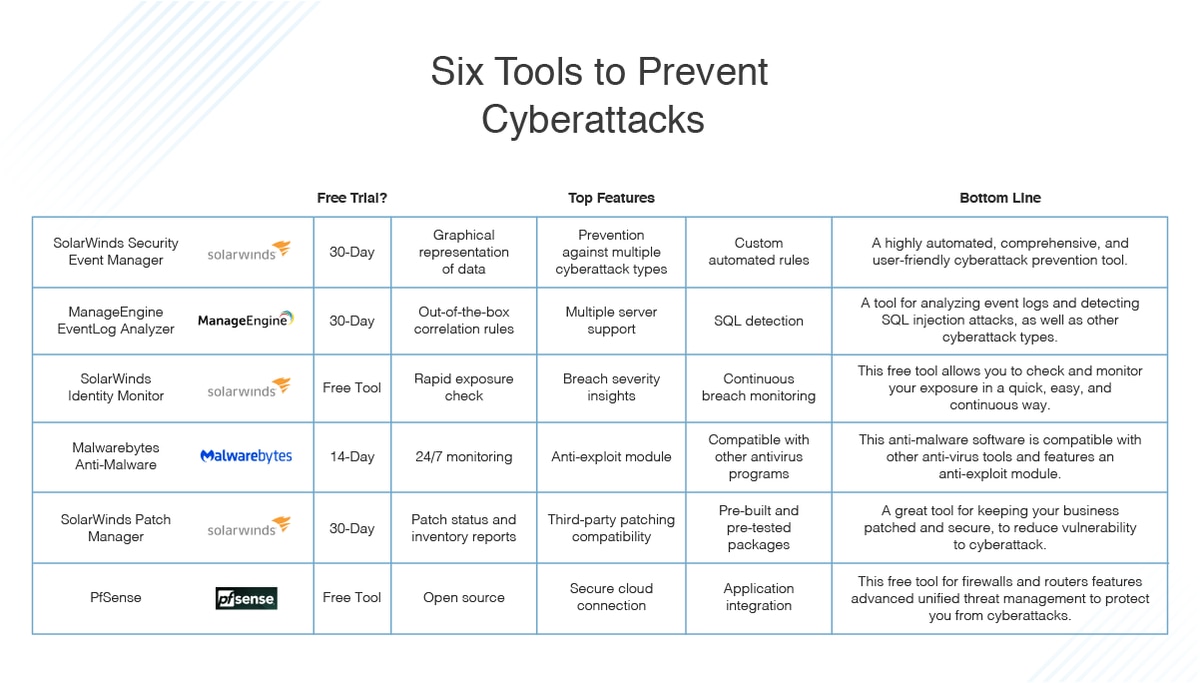
Top 6 Common Types Of Cyberattacks Dnsstuff
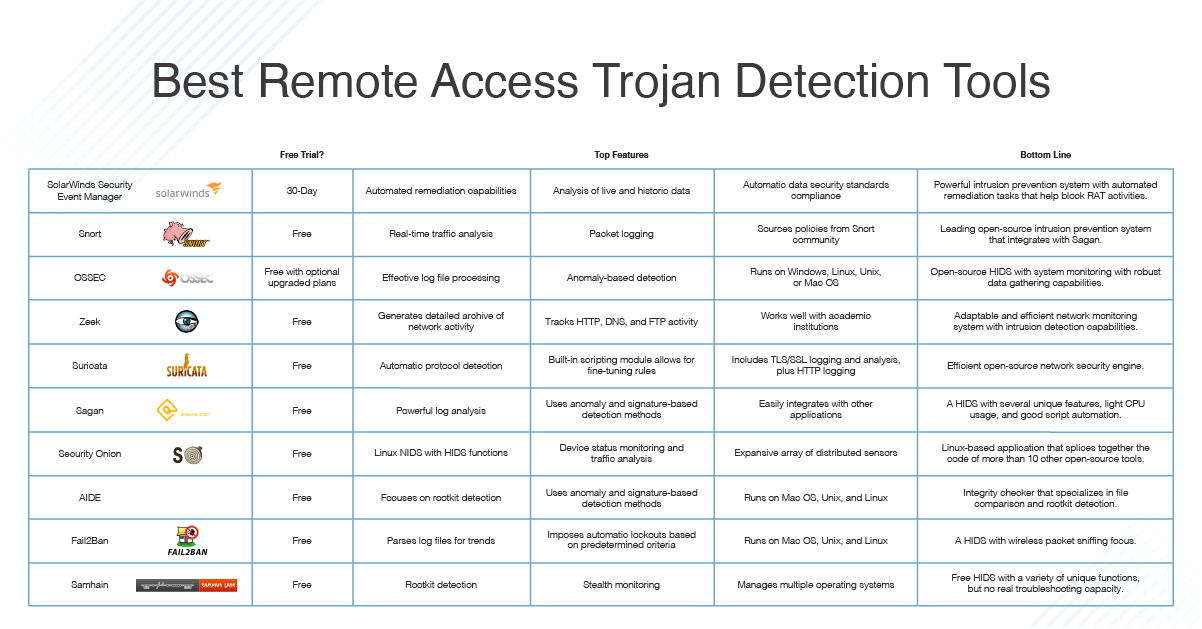
Remote Access Trojan Detection Software Rat Protection Guide Dnsstuff

Hassh A Network Fingerprinting Standard Which Can Be Used To Identify Specific Client And Server Ssh Implementations Networking Server Cyber Security

Passhunt Tool For Searching Of Default Credentials For Network Devices Web Applications And More Best Hacking Tools Web Application Hobbies For Adults
Comments
Post a Comment